You've set up authentication in your Next.js application, but users keep getting logged out unexpectedly. You've triple-checked your code, yet the redirect to the homepage happens before the cookie is fully set. No matter what you try, the session doesn't exist for that crucial moment, breaking your entire authentication flow.
You've set up authentication in your Next.js application, but users keep getting logged out unexpectedly. You've triple-checked your code, yet the redirect to the homepage happens before the cookie is fully set. No matter what you try, the session doesn't exist for that crucial moment, breaking your entire authentication flow.
Sound familiar? Cookie management in Next.js can be frustratingly complex, especially when dealing with authentication, server components, and client-side interactions. But with the right approach, you can build robust, secure cookie implementations that enhance both security and user experience.
Understanding Cookie Fundamentals in Next.js
Cookies serve as the backbone of session management and user preferences in web applications. In Next.js applications, they play an even more crucial role due to the framework's hybrid rendering approach.
Types of Cookies You Need to Know
Session cookies: Temporary cookies that expire when the browser closes
Persistent cookies: Long-lived cookies with a specific expiration date
HttpOnly cookies: Security-enhanced cookies inaccessible to JavaScript
Secure cookies: Cookies transmitted only over HTTPS connections
SameSite cookies: Cookies with restrictions on cross-site requests
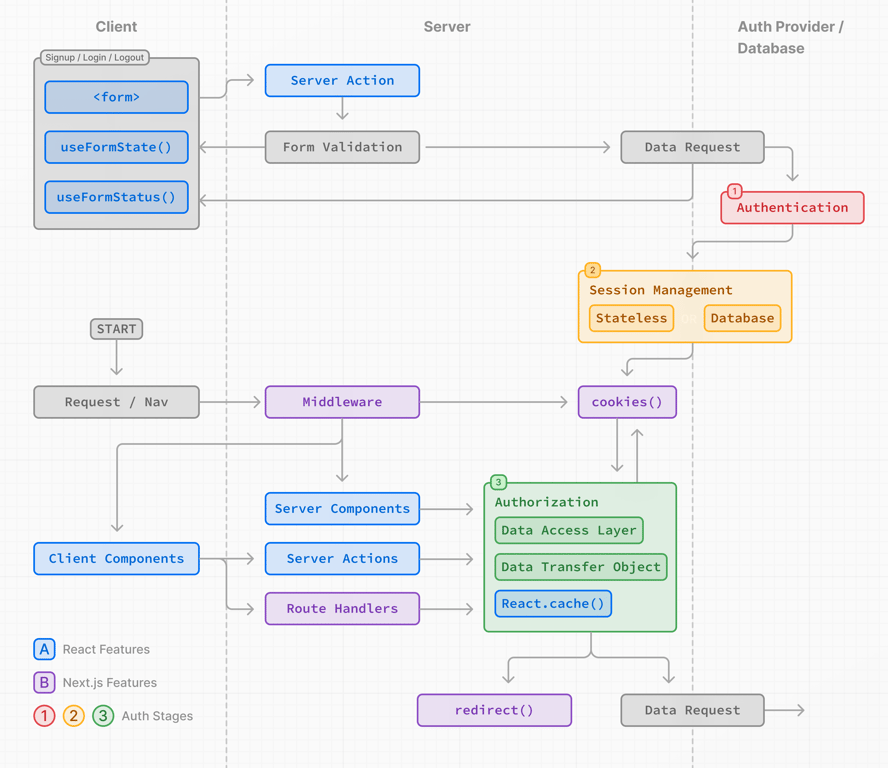 Understanding these distinctions is vital because choosing the wrong cookie type can lead to security vulnerabilities or broken user experiences. For example, using regular cookies instead of HttpOnly cookies for authentication tokens exposes your users to cross-site scripting (XSS) attacks.
Understanding these distinctions is vital because choosing the wrong cookie type can lead to security vulnerabilities or broken user experiences. For example, using regular cookies instead of HttpOnly cookies for authentication tokens exposes your users to cross-site scripting (XSS) attacks.
Common Cookie Management Pain Points in Next.js
Before diving into implementation, let's address the most common frustrations developers face:
1. The Cookie Race Condition
One of the most notorious issues is the dreaded "cookie race condition," where redirects happen before cookies are fully set.
// This approach often fails
async function handleLogin() {
const response = await login(credentials);
if (response.success) {
// Cookie might not be fully set when redirect happens
window.location.href = '/dashboard';
}
}
As one developer described on Reddit: "The redirect to the homepage happens before the cookie is fully set/available." This timing issue breaks authentication flows and leads to poor user experiences.
2. Manual Cookie Handling Overhead
Another common complaint is the need to manually parse and attach cookies:
"I need to manually parse the cookie, and attach it to the fetch function as a header," shared a frustrated developer. This becomes especially painful when working with separate backends like Django or Express.
3. HTTP-Only Cookie Limitations
HTTP-only cookies enhance security but complicate frontend management:
"I'm having trouble manipulating these cookies when they need to be refreshed or deleted on the frontend side," noted another developer working with a Django backend.
Best Practices for Setting Cookies in Next.js
Now let's explore how to properly set cookies in Next.js applications to avoid these common pitfalls.
Server-Side Cookie Setting
For maximum security, especially with authentication tokens, set cookies server-side:
// In an API route (pages/api/login.js or app/api/login/route.js)
export async function POST(request) {
// Authentication logic here
const response = NextResponse.json({ success: true });
// Set the cookie properly with security attributes
response.cookies.set({
name: 'sessionToken',
value: 'your-jwt-token-here',
httpOnly: true,
secure: process.env.NODE_ENV === 'production',
sameSite: 'lax',
path: '/',
maxAge: 60 * 60 * 24 * 7 // 1 week
});
return response;
}
The key security attributes to include are:
httpOnly: trueto prevent JavaScript accesssecure: true(in production) to ensure HTTPS-only transmissionsameSite: 'lax'to provide CSRF protection while allowing normal navigationAppropriate
maxAgeto limit the cookie's lifespan
Client-Side Cookie Setting
For non-sensitive data like UI preferences, client-side cookie setting is acceptable:
import Cookies from 'js-cookie';
// Setting a cookie for theme preference
function setThemePreference(theme) {
Cookies.set('theme', theme, {
expires: 365, // 1 year
path: '/',
sameSite: 'lax'
});
}
Libraries like js-cookie simplify client-side cookie management and provide a cleaner API than the native document.cookie.
Solving the Cookie Race Condition
To prevent the dreaded race condition where redirects happen before cookies are set, implement one of these strategies:
Strategy 1: Add Cookie to Auth Response, Only Redirect on Success// Client component
'use client';
import { useState } from 'react';
import { useRouter } from 'next/navigation';
export default function LoginForm() {
const router = useRouter();
const [isLoading, setIsLoading] = useState(false);
async function handleSubmit(e) {
e.preventDefault();
setIsLoading(true);
const formData = new FormData(e.target);
const response = await fetch('/api/login', {
method: 'POST',
body: formData,
credentials: 'include' // Important for cookies
});
const data = await response.json();
if (data.success) {
// Short delay to ensure cookie is set
setTimeout(() => {
router.push('/dashboard');
}, 100);
} else {
setIsLoading(false);
}
}
// Form JSX
}
This approach adds a small delay before redirecting, giving the browser time to process the cookie. While not elegant, it's effective in most cases.
Strategy 2: Verify Cookie Presence Before Redirectingasync function handleLogin() {
const response = await login(credentials);
if (response.success) {
// Create a function to check if cookie exists
const checkCookie = () => {
// For non-HttpOnly cookies
const hasCookie = document.cookie.includes('sessionToken=');
if (hasCookie) {
window.location.href = '/dashboard';
} else {
// Check again after a short delay
setTimeout(checkCookie, 50);
}
};
checkCookie();
}
}
This recursive approach checks for the cookie's presence before redirecting, ensuring the authentication flow works reliably.
Reading Cookies Effectively in Next.js
Retrieving cookies differs between server and client components, each with its own approach.
Server-Side Cookie Reading
In server components or API routes, use the built-in methods:
// In a Server Component
import { cookies } from 'next/headers';
export default async function Dashboard() {
const cookieStore = cookies();
const sessionToken = cookieStore.get('sessionToken');
if (!sessionToken) {
// Handle unauthenticated state
redirect('/login');
}
// Fetch user data using the session token
const userData = await fetchUserData(sessionToken.value);
return (
<div>
<h1>Welcome, {userData.name}</h1>
{/* Dashboard content */}
</div>
);
}
For pages using the older Pages Router:
// In getServerSideProps
export async function getServerSideProps(context) {
const { req } = context;
const sessionToken = req.cookies.sessionToken;
if (!sessionToken) {
return {
redirect: {
destination: '/login',
permanent: false,
},
};
}
// Rest of your code
return {
props: { /* your props */ }
};
}
Client-Side Cookie Reading
For client components, you have multiple options:
Using js-cookie:'use client';
import { useState, useEffect } from 'react';
import Cookies from 'js-cookie';
export function ThemeToggle() {
const [theme, setTheme] = useState('light');
useEffect(() => {
// Read the theme preference from cookie
const savedTheme = Cookies.get('theme') || 'light';
setTheme(savedTheme);
}, []);
// Toggle logic
}
If you're using Next-Auth or a similar authentication library:
'use client';
import { useSession } from 'next-auth/react';
import { redirect } from 'next/navigation';
export default function ProtectedClientComponent() {
const { data: session, status } = useSession();
if (status === 'loading') {
return <div>Loading...</div>;
}
if (status === 'unauthenticated') {
redirect('/login');
}
return (
<div>
<h1>Hello, {session?.user?.name}</h1>
{/* Protected content */}
</div>
);
}
Creating a Robust authFetch Function
To simplify cookie handling for authentication, create a reusable authFetch function:
// utils/authFetch.js
export async function authFetch(url, options = {}) {
const defaultOptions = {
credentials: 'include', // Automatically include cookies
headers: {
'Content-Type': 'application/json',
...options.headers,
},
};
const mergedOptions = {
...defaultOptions,
...options,
headers: {
...defaultOptions.headers,
...options.headers,
},
};
const response = await fetch(url, mergedOptions);
// Handle token refresh if needed
if (response.status === 401) {
// Attempt to refresh token
const refreshed = await fetch('/api/auth/refresh', {
method: 'POST',
credentials: 'include',
});
if (refreshed.ok) {
// Retry the original request
return fetch(url, mergedOptions);
} else {
// Redirect to login if refresh fails
window.location.href = '/login';
return response;
}
}
return response;
}
This function handles common authentication patterns like cookie inclusion and token refresh, addressing the manual cookie handling pain point that many developers face.

Advanced Cookie Management Techniques
Using Middleware for Centralized Cookie Handling
Next.js middleware offers powerful capabilities for cookie management before the request reaches your components:
// middleware.js
import { NextResponse } from 'next/server';
export function middleware(request) {
const response = NextResponse.next();
// Check for authentication
const sessionToken = request.cookies.get('sessionToken');
// Protected routes pattern
if (
request.nextUrl.pathname.startsWith('/dashboard') &&
(!sessionToken || isTokenExpired(sessionToken.value))
) {
// Redirect unauthenticated users
return NextResponse.redirect(new URL('/login', request.url));
}
// You can also set cookies in middleware
if (request.nextUrl.pathname === '/api/login') {
response.cookies.set({
name: 'lastLoginAttempt',
value: new Date().toISOString(),
path: '/',
});
}
return response;
}
// Only run middleware on specific paths
export const config = {
matcher: ['/dashboard/:path*', '/api/:path*']
};
Middleware provides a cleaner approach to authentication checks and can reduce redundancy across your application.
Handling JWT Token Length Issues
As mentioned by one developer on Reddit, large JWT tokens can cause problems:
"It turned out the token I was retrieving in my auth response and setting to a cookie was too large for a single cookie (too many permission claims on the JWT token)."
To solve this:
Minimize token claims: Only include essential data in your JWT payload
Split large tokens: If necessary, split tokens across multiple cookies:
function setLargeToken(token) {
// Maximum safe cookie size is around 4KB
const maxSize = 4000;
if (token.length <= maxSize) {
// Set as single cookie if it fits
response.cookies.set('token', token, cookieOptions);
} else {
// Split token into chunks
const chunks = Math.ceil(token.length / maxSize);
for (let i = 0; i < chunks; i++) {
const start = i * maxSize;
const end = Math.min(start + maxSize, token.length);
const chunk = token.substring(start, end);
response.cookies.set(`token_${i}`, chunk, cookieOptions);
}
// Store the number of chunks
response.cookies.set('token_chunks', String(chunks), cookieOptions);
}
return response;
}
To retrieve a split token:
function getLargeToken(cookieStore) {
const singleToken = cookieStore.get('token');
if (singleToken) {
return singleToken.value;
}
const chunksCount = Number(cookieStore.get('token_chunks')?.value || '0');
if (chunksCount > 0) {
let token = '';
for (let i = 0; i < chunksCount; i++) {
const chunk = cookieStore.get(`token_${i}`)?.value || '';
token += chunk;
}
return token;
}
return null;
}
Cookie Security Best Practices
To ensure your Next.js application's cookies are secure:
Always use HttpOnly for sensitive cookies: This prevents client-side JavaScript from accessing the cookie, mitigating XSS attacks
Implement proper CSRF protection: Even with SameSite cookies, implement CSRF tokens for sensitive operations
Set appropriate cookie lifetimes: Short-lived session cookies are generally more secure than long-lived persistent cookies
Use secure cookies in production: The
secureflag ensures cookies are only sent over HTTPSImplement token rotation: Regularly refresh authentication tokens to limit the damage from potential token theft
Conclusion
Implementing robust cookie management in Next.js requires understanding both the framework's unique capabilities and general web security principles. By following these best practices, you can avoid common pitfalls like race conditions, reduce manual overhead, and create a secure, seamless experience for your users.
Remember these key takeaways:
Set sensitive cookies server-side with proper security attributes
Implement strategies to prevent cookie race conditions during authentication
Create helper functions like
authFetchto simplify cookie handlingUse middleware for centralized authentication checks
Be mindful of cookie size limitations, especially with JWT tokens
Always prioritize security with HttpOnly and Secure flags
With these approaches, you'll build Next.js applications that maintain secure user sessions while providing excellent user experiences.
For more detailed information, check out these resources: